top of page
Healthy Lifestyle with Ayurveda
The Ancient Indian Science "Ayurveda" believes in maintaining the health of a healthy person and treating the diseased person. Ayurveda...
Nov 30, 20233 min read

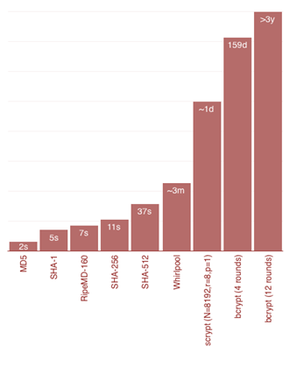
Choose Password Hashing Algorithm
Introduction The goal of a strong password strategy is to mitigate data breaches in the application. The essence of authentication is to...
Nov 30, 20233 min read
Cyber Security : Tools and Techniques
The world is more dependent on technology than ever before because of the proliferation of digital data. No matter how big or small,...
Nov 30, 20234 min read
Social Networking and Social Media Security
Introduction: Social networking is building upon the basic concept of traditional social networks using which users can connect...
Nov 30, 20235 min read
All About Malware
Malware is commonly known for malicious software. It is a code delivered by a network to interfere with the normal functioning of a...
Nov 30, 20234 min read
Black Cat
I got down at Sanjan from an overcrowded train. It was the only available train that had a scheduled stop at this nondescript village. It...
Nov 30, 20234 min read
bottom of page
